Computer Necessities
According to Darris!
A must! I highly, highly recommend that everyone subscribe to the Kim Komando newsletter. Kim has a radio show on the weekends for three hours. She answers common computer questions, discusses issues of security, wireless services, CD and DVD recording, Microsoft updates and just about anything else you could think of regarding computers. Her website offers you up to three free e-mails. The first is the weekly newsletter, which is a must for computer users in my opinion. The others, such as the Daily Tip, are helpful and optional. Reading the main newsletter will help acquaint you with the computer, computer jargon, and computer issues in general. It is easy to read and you can simply skip the advertisements. Her radio show is heard on the Horn Radio Network in the Knoxville area on 850 AM. It airs on Saturday from 10:00 a.m. until 1 p.m. You can find local listings by accessing her website.
A must! Before you go any further into computer use, you must learn about Firewalls. Firewalls prevent access to your computer when you are on the Internet. Windows XP has a built-in firewall, but older versions of Windows do not. If you have Windows XP, the firewall is NOT automatically turned on—you must do it!
To Firewall Windows XP- Start
- Connect To
- Right Click on your connection, select Properties
- Click the Advanced tab.
- Check the Firewall box.
If you have any trouble doing this, then go to My Computer, Control Panel, Network and Internet Connections, Network Connections, then Right click on your connection and select Properties, the Advanced tab, and check the Firewall box.
There have been cases where no Firewall tab appeared. In such cases I recommend going to the Add or Remove Programs option in the Control Panel and select Add/Remove Windows Components then remove Network Services and then reinstall it. This may bring back the Firewall tab.
Firewall OptionsIf you do not have Windows XP or if you want more firewall protection than Windows XP offers, you can get one of two popular programs free from the Internet. ZoneAlarm and Outpost are both good. There are commercial versions available, but the free ones work well enough for most people. Both of these are available on my disk of free programs under the My Programs link.
Understanding FirewallsThink of portholes on a ship. If a ship has open portholes they would let water in. Likewise, when you access the Internet your computer has a number of ports open through which traffic can flow back and forth. Hackers try to find these open ports and then send you a “virus” or a “Trojan horse” which infects your computer and makes it a “zombie” for the hacker to use as he wishes. Often you will never know it is going on! The hacker may use your computer to send e-mails and further spread his virus or Trojan. A firewall “hides” these ports from the hackers so that they cannot access your computer.
The Windows XP firewall only prevents access from outside your computer (through the Internet), but both ZoneAlarm and Outpost have an additional feature which can be helpful. They prevent programs on your computer from accessing the Internet without your permission. Many Trojans do this if they are already on your computer. If you install one of these firewalls, then you will have to determine which programs you will permit to access the Internet. This can be confusing for beginning computer users who do not know much about the files and programs. My recommendation is that you use the firewall that comes with Windows XP and then scan your computer for viruses, Trojans, and spyware. When the computer is “clean” then you will only need to guard against what you put on the computer. That means that it is not necessary to have a firewall to “check” everything that wants to access the Internet from your computer. My experience has been that Windows XP is enough (and less hassle) if you scan your computer once a week and scan the programs you load or download.
How You Get VirusesViruses come to you in various ways.
- If your computer is not firewalled, then a hacker may sneak one onto your computer via the Internet. They have automated programs that look for open ports.
- If you download a program from the Internet and install it without first scanning it for viruses, then if may have a virus bundled with it.
- If you install programs, particularly games, that come from unknown sources or from a “friend” or let your kids or grandkids do the same, then these may contain viruses. They need to be scanned first and then the computer should be re-scanned after they are installed.
- E-mail often comes with “attachments.” Attachments may be any number of things: pictures, music, programs, documents, screen savers, etc. Often, these are harmless. But, you should not open anything that you were either not expecting or not from someone you know. It is best to have a virus scanner that automatically scans all incoming and outgoing e-mail. This way you will know whether or not the attachment contains a virus.
- Pop-up ads are annoying but have been harmless until recently. Hackers got into some ad agency sites and infected their pop-up ads with a virus (June 2004). This virus will record keystrokes if you visit one of 50 financial sites and is an attempt to steal your passwords and account information and send them to a website in Estonia. This targets only the Internet Explorer browser, so if you use another browser you are safe. If you have updated your IE browser with an April 2004 update you are also safe, and if you have installed the MSN toolbar or the Google toolbar or some similar thing that blocks pop-up ads you are safe.
In addition to having a virus scanner that checks your incoming and outgoing e-mail, other tips can clue you to suspicious e-mail.
-
If you do not know the person sending it and it has an attachment, then do not open the attachment.
-
If it comes from someone you know, but you are not expecting it or it sounds strangely written then ask the person before opening it. E-mail viruses often originate from overseas and the English is usually poorly written. A sentence like “I want you have this.” is typical of the mistakes non-English speakers make.
-
Virus writers are getting more creative these days. They try to write “official” looking e-mail to “fake you off.” I've had email that purportedly comes from PayPal, E-Bay, Yahoo, and even is allegedly “returned” e-mail that I've sent. In each case, they are being deceptive. No reputable company sends you a request to update your information, such as the scams with E-Bay and PayPal. When a piece of mail comes to me that says it is “returned” because it failed to send, I check the e-mail address in the body of the message. If it is not one in my address book, then I know I didn't send it and it is a scam. Such mail will always contain a virus-infected attachment they want you to open.
BHOs have caused many problems within families because a wife may assume that her husband has been accessing pornographic websites or the parents may suspect a child is doing so when it is simply the BHO doing what it does. Stories of near divorce have been heard because of the BHOs.
Spyware, Adware, and MalwareUnbeknownst to most people, your computer may have a “lesser” form of infestation. Spyware or Adware are a means of keeping records of where and what you do on the Internet. This information is then sent back to someone so that they may target you with advertisements. Malware is a similar thing, only it may be potentially malicious, but not a virus per se.
Sometimes programs you download and install require that you agree to receive some sort of advertisement. A good example is Download Accelerator, which is a download manger. This program has harmless ads that “pay” for the program so that you can use it for “free.” Many such “free” programs exist. The main “downside” to such a program is that it takes up Internet bandwidth to transfer the ads and that slows down your Internet connection. Spyware and Malware are different stories. It is important to read the EULA (End User License Agreement) when installing “free” programs to learn whether or not it contains Adware or Spyware. Malware may or may not be mentioned in the EULA. A quicker route to the same information is to do an online search for reviews of the program. Usually reviewers will tell you whether or not the program has any kind of “ware.”
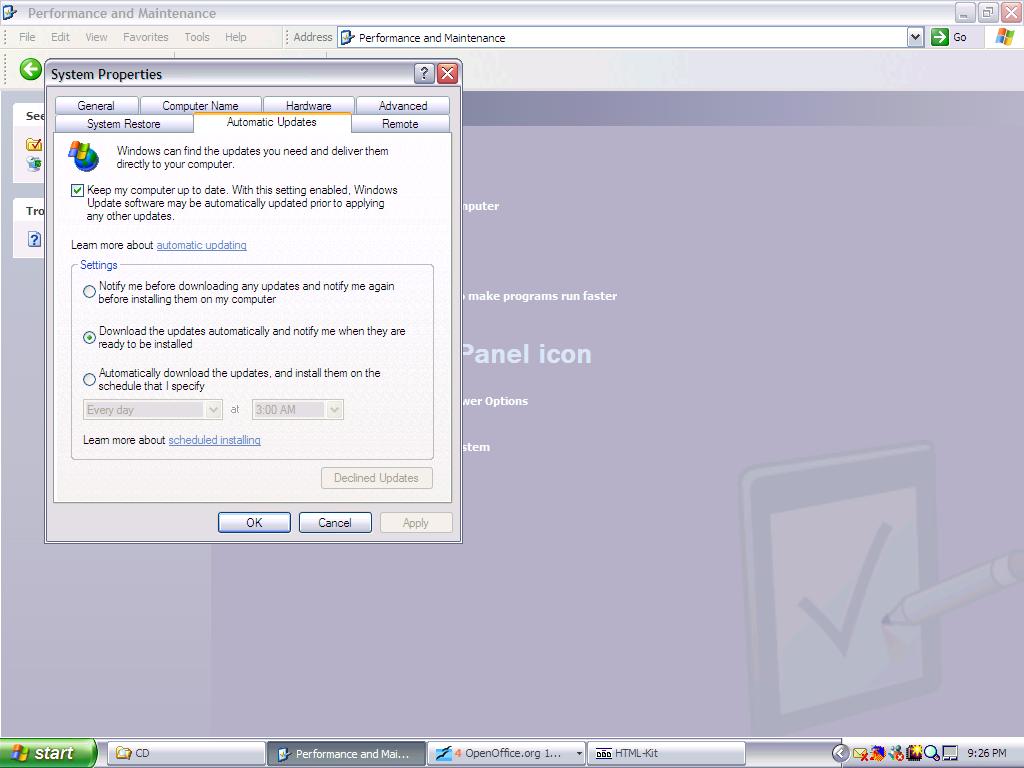
Automatic UpdateOnce you have firewalled and scanned your computer for viruses and spyware, then you need to be certain that the Automatic Update is enabled and you have all the Critical Updates that Microsoft has to offer.
- Click Start
- My Computer
- Control Panel
- Performance and Maintenance
- System
- Automatic Update tab.
- Unless you leave your computer running 24 hours a day, then I suggest that you select the box “Keep my computer up to date” and then the middle setting “Download the updates automatically and notify me when they are ready to be installed.” This will download the Critical Updates from Microsoft as they become available. Critical Updates are also known as “patches” which fix “holes” in the “security” of the software. Windows XP users will have a balloon pop up in the lower right corner which says “You have updates ready to install.” Click on the balloon and install the updates. You may have to reboot the computer, so save any work that you are doing.
You can also manually update your computer by starting Internet Explorer, clicking Tools and Windows Update. This will take you to the Microsoft website where you can scan for any recent updates.
One nice feature of the automatic update is that if you disconnect from the Internet before it is finished, it will pick up where it left off the next time.
Spam and SpammersSpam is a term that is used for unwanted and unsolicited e-mail. The name was adopted from the Hormel pork product by people who had a less than favorable view of it. After all, who wants Spam when you can have Ham? Hence, Spam has become the term for the unwanted “junk mail” and Ham has become the term for the e-mail that you want. Spam is an annoyance because it clutters up your mailbox. It is usually not carrying a virus but, instead, is advertising something. It may something as inoffensive as cheap software, mortgage rates, or used car websites or it may carry pornographic pictures or advertise for pornographic websites.
Spam FiltersMany Spam filter programs have arisen in response to this problem. Spam filtering programs use various methods to try and identify unwanted e-mail. A filter can be used to create a very restrictive list of approved e-mails. For example, only people who are already in your computer's Address Book may be permitted to send you e-mail. This is known as a White List. A Black List would be of senders who are forbidden to send you e-mail. But most filtering programs “learn” from the e-mail sent to you or from pre-existing filters they contain. This method is not foolproof and spammers have been been getting creative lately to try and fool the Spam filters. Consider just the following spellings of Viagra that have come to my mailbox:
V-IAA.GRA,Via]gra, v1aGr@, v-i-a.grr-a , VIAwGRA
You can quickly see how difficult it is for Spam filters to keep up with such unconventional spellings. Spammers also use images in the e-mail to carry their message, which avoids the spelling function of the Spam filters. Therefore, people have adapted their filters to try and catch these.
How do spammers get my e-mail address?There are several basic ways that a spammer can get your e-mail address.
They have programs that generate random e-mail addresses and eventually they will generate yours. There is nothing you can really do to prevent this aside from having a really strange mixture of letters and numbers as your address.
If you belong to a newsgroup, then they have been able to get names and/or e-mails from them. Most good newsgroups will allow you to hide your e-mail address. It is best if you belong to one to use a “user name” that is not the same as your e-mail address. Spammers can get those names and then attach a number of e-mail suffixes to them, such as @aol.com or @bellsouth.com and eventually hit your e-mail address.
If you have a personal webpage with the e-mail address on it, then spammers can get it from that page using a program that searches for them.
Forwarded e-mail. Everybody has a friend who forwards them e-mail with touching stories, prayers, or humorous material. We've all seen the long list of e-mail addresses at the top of those e-mails and we have to scroll way down the page to get to the actual story. If that e-mail wound up in the hands of a spammer he could glean the e-mail addresses right off of it. Therefore, if you send forwarded e-mail, first delete everything except the actual story itself. Second, if you send it to more than one person, send it as as Blind Carbon Copy (BCC) not as a To: or CC:. The reason for this is simple. A BCC hides the e-mail addresses and they will not show up when the person on the other end receives the e-mail. To do this in Outlook, just click the Forward button then click the word “To:” and it will bring up a box that has the BCC option. One other tip. If you regularly send to groups, such as friends or family or even office staff, I urge you to set up a “group.” This will save you from having to select the e-mail address each time.
There is one other standard way that spammers can get your e-mail address, and that is if you give it to them. Spammers are incredibly clever and devious people. They are increasingly making Spam mail that looks like real e-mail. One of the tricks they put in almost every e-mail is the “remove” line. They offer you an opportunity to “click here to be removed” from their mailing list. Unfortunately, that is only a trick. Never, ever, ever try to unsubscribe from a Spam. They typically ask you to enter the e-mail address you want to cancel. What that does is give the spammer your real and active e-mail address. They love this because they have a “hot” address in their hands. You can guarantee that they'll send you more Spam and that the list will be sold to other spammers. In June of 2004 an employee of AOL was arrested for stealing 92 million AOL e-mail addresses and selling them to a spammer. There is a lot of money to be made by spammers if they have enough good e-mail addresses. Eventually they will sell somebody something. Stiff fines are imposed on people who do send Spam, but that has not curbed the business to date.
For
more on Spam and how spammers can get your e-mail address see:
this government site or this private site.
This website has an interesting list of sites to help you track down a
spammer. It is not necessary to track the spammer, however, you
can have some good results by installing a Spam filter. See
PC Programs.